Your wireless light switch runs for 5 years on a coin battery. Your motion sensor never needs charging. How? The answer is Zigbee, a wireless communication protocol specifically designed for low power, low cost devices in the Internet of Things (IoT) ecosystem.
What is Zigbee?
Zigbee is a wireless mesh networking standard that enables smart devices to communicate with each other while consuming the bare minimum in terms of power. Launched in the early 2000s, it has become the backbone of countless smart home systems, from IKEA’s Trådfri lighting to Amazon Echo hubs. Gadgets running this clever little protocol can operate for months or even years on a single battery.
The Zigbee protocol stack consists of four primary layers that work together, including:
- Physical layer
- Medium Access Control (MAC) layer
- Network layer (NWK)
- Application layer (APL)
The Physical and MAC layers follow the IEEE 802.15.4 standard, handling how devices physically transmit and receive signals. Zigbee builds on top of this foundation, adding network management and application support. Security is baked right in. All communications are automatically encrypted using strong 128-bit AES encryption, so only authorized devices can decode the messages.
Evolution of Zigbee Technology
Since its inception, Zigbee has continued to evolve to meet the growing demands of the smart home and industrial IoT markets. Here’s a quick look at how this protocol has developed over the past two decades.
| Year | Milestone |
|---|---|
| 2003 | IEEE approved the foundational IEEE 802.15.4 standard, establishing the physical and MAC layer specifications for Zigbee |
| 2005 | Zigbee 2004 specification (Zigbee 1.0) was publicly released, marking the first complete protocol stack for low power wireless personal area networks (PANs) |
| 2006 | Zigbee 2006 enhanced the original specification and introduced cluster libraries for standardized device interactions |
| 2007 | Zigbee Pro (Zigbee 2007) brought major improvements for larger, more reliable networks while maintaining backward compatibility with earlier devices |
| 2015-2016 | Zigbee 3.0 unified multiple application profiles into a single standard, dramatically improving interoperability between manufacturers and simplifying certification |
| 2023 | Zigbee PRO 2023 brought major security upgrades including smarter encryption keys, device screening before joining networks and the ability to replace your hub without re-pairing all devices, in addition to expanded support for longer range frequencies |
This evolution shows Zigbee’s commitment to staying relevant. Unlike some protocols that fragment over time, Zigbee has consistently improved while maintaining compatibility. This means your older devices can usually work happily alongside the newest additions to your smart home.
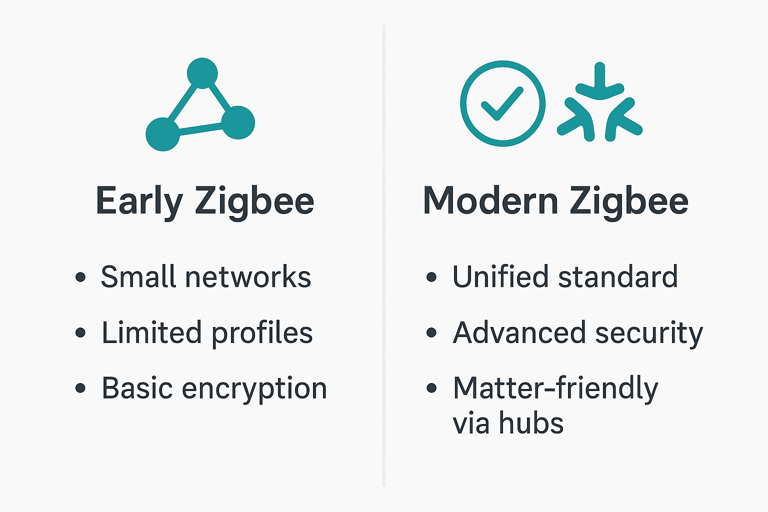
Zigbee Compared to Other Protocols
So where does Zigbee fit in amongst the diverse wireless protocol landscape?
| Feature | Zigbee | Wi-Fi | Z-Wave | Bluetooth |
|---|---|---|---|---|
| Range | 10-100m (mesh extends further) | 50m+ | 30-100m | 10-100m |
| Power Consumption | Very Low | High | Very Low | Low to Medium |
| Data Rate | 250 kbps | Up to 10+ Gbps | 100 kbps | 1-3 Mbps |
| Network Size | Up to 65,000+ devices* | ~250 devices (consumer routers) | 232 devices (classic) ~4000 devices (Z-Wave LR) | Classic: ~7 BLE: 100s+ |
| Frequency | 2.4 GHz (global) | 2.4/5 GHz | 900 MHz (varies by region) | 2.4 GHz |
| Best For | Smart home, sensors, battery devices | Video, high bandwidth | Home automation | Wearables, audio |
*Note: The 65,000+ device figure represents Zigbee’s theoretical 16-bit address space. In practice, coordinator hardware limitations (child tables, routing tables, memory) typically support hundreds to low thousands of devices per network. Real world deployments rarely exceed a few hundred devices per coordinator.
Quick Decision Guide: Which Protocol Should You Choose?
Stuck on which wireless protocol fits your needs? Here’s a quick reference to help you decide.
Zigbee is a good choice when:
- You need battery powered sensors and devices (months to years of battery life)
- Building a mesh network with many devices (lighting, sensors, switches)
- Cost is a priority (Zigbee devices are typically affordable)
- You want proven reliability with huge device selection
When to choose Thread:
- You’re building a new smart home and want native Matter support
- You like Zigbee’s benefits but want IP based networking
- You’re committed to the Apple/Google/Amazon Matter ecosystem
Consider Z-Wave when:
- You’re in North America and prefer 900 MHz (less Wi-Fi interference)
- You want a smaller, more controlled device ecosystem
- Regional frequency differences don’t concern you (Z-Wave varies by country)
Pick Wi-Fi if:
- You need high bandwidth (cameras, video doorbells, streaming)
- You already have excellent Wi-Fi coverage
- You don’t mind higher power consumption (devices stay plugged in)
- Simplicity matters (no hub needed, works with existing router)
Real World Applications of Zigbee
Millions of devices worldwide rely on Zigbee. Here’s where you’ll find this protocol making a notable difference.
Home Automation
This is where Zigbee truly dominates. Popular smart home brands have embraced Zigbee because it simply works.
- Smart Lighting: Philips Hue, IKEA Trådfri, Sengled, Aqara, Sonoff and GE smart bulbs use Zigbee to create responsive, color-changing lighting systems that can run for years without battery changes in wireless switches
- Security Systems: Door sensors, window contacts, motion detectors and smart locks from brands like Samsung SmartThings and Aqara rely on Zigbee’s reliability and low power consumption
- Climate Control: Zigbee based thermostats and TRVs (thermostatic radiator valves) from Hive (UK), Danfoss Ally, Schneider Wiser and Tuya/Moes communicate with remote temperature sensors throughout your home
- Smart Hubs: Amazon Echo (4th gen and newer), Samsung SmartThings and Hubitat Elevation all include built-in Zigbee radios to control your devices
For detailed recommendations across these categories, from smart plugs and sensors to lighting and switches, see our complete guide to the best Zigbee smart home devices.
Industrial Controls
Zigbee is also used in commercial building and light industrial applications.
- Energy management systems tracking consumption across facilities
- Real-time asset tracking for inventory and equipment in warehouses
Understanding the Zigbee Protocol Stack
Want to understand why Zigbee is so reliable? Let’s peek under the hood. The Zigbee protocol stack consists of four distinct layers, each handling specific communication tasks.
Physical Layer (PHY)
The Physical Layer is where all the magic starts. This layer manages the actual radio transmission and reception.
Key Responsibilities
- Data Transmission: Converts digital data into radio waves that can travel through the air. The signals are spread across the bandwidth to make them more resistant to interference from other devices
- Modulation: Uses a smart signaling method (called O-QPSK) for the 2.4 GHz band that’s both energy efficient and reliable, achieving speeds of 250 kbps
- Channel Management: Operates across 16 channels in the 2.4 GHz frequency band, automatically selecting the clearest channel to avoid interference from Wi-Fi routers, microwaves and other wireless devices
The 2.4 GHz band is globally available without licensing, which is why your Zigbee devices work whether you bought them in New York, London or Tokyo.
Zigbee also supports sub-GHz frequencies (lower frequencies like 868 MHz in Europe with 1 channel and 915 MHz in the Americas with 10 channels) that trade speed for better range and ability to penetrate walls. These are ideal for outdoor sensors, large buildings or challenging environments, though most home devices typically stick with 2.4 GHz.
Medium Access Control (MAC) Layer
The MAC Layer acts like a traffic controller, making sure devices don’t talk over each other. It also follows the IEEE 802.15.4 standard and works hand-in-hand with the Physical Layer.
Key Responsibilities
- Data Framing: Packages data into structured frames with addressing information, making it easy to identify the sender and recipient
- Collision Avoidance: Implements Carrier Sense Multiple Access/Collision Avoidance (CSMA/CA). Before transmitting, devices “listen” to make sure the channel is clear (like checking for traffic before entering a highway)
- Network Coordination: Manages beacon transmissions for synchronized networks and handles device associations
- Basic Security: Provides frame integrity and encryption at the link level
Network Layer (NWK)
Here’s where Zigbee gets interesting. The Network Layer, developed by the Zigbee Alliance (now the Connectivity Standards Alliance), is what gives Zigbee its mesh networking superpowers.
Key Responsibilities
- Mesh Networking: Creates self-healing networks where messages can hop from device to device to reach their destination. If one device fails, the network automatically finds an alternate path
- Routing: Determines the best path for messages to travel through the mesh network using algorithms that balance network load and minimize hops
- Network Formation: Allows a coordinator device to establish a new network and manage joining devices
- Address Assignment: Distributes unique network addresses to devices as they join
The mesh capability is what allows Zigbee networks to cover large areas. A single Zigbee coordinator might only reach 30 meters, but with additional router devices extending the network, you can cover an entire house, building or campus.
Application Layer (APL)
The Application Layer handles what your devices actually do. It defines whether a device is a light, sensor or lock, and how it behaves. It consists of the three components below.
Application Framework (AF)
- Hosts up to 240 Application Objects that define device behaviors
- Each Application Object represents a specific device function (like “dimmable light” or “temperature sensor”)
Zigbee Device Object (ZDO)
- Manages network discovery and security
- Handles device initialization and configuration
- Controls binding, which is the process of creating communication relationships between devices
Application Support Sub-layer (APS)
- Provides reliable data transfer services
- Manages group addressing for controlling multiple devices simultaneously
- Handles fragmentation for larger messages

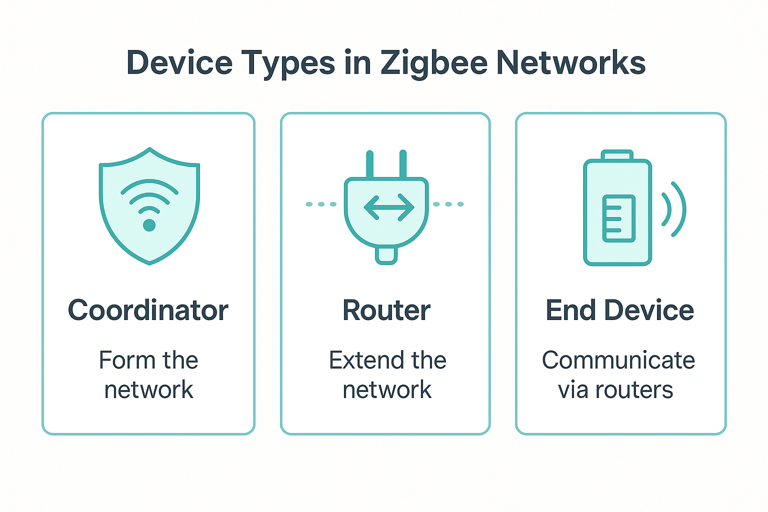
Device Types in Zigbee Networks
Zigbee networks include three types of devices, each with distinct roles.
Zigbee Coordinator (ZC)
Every Zigbee network must have exactly one coordinator. This device:
- Initiates and manages the network
- Assigns network addresses to joining devices
- Stores network security keys
- Acts as the trust center for security
- Often remains powered continuously (not battery operated)
In smart home setups, your hub (like an Echo or SmartThings) typically acts as the coordinator.
Zigbee Router (ZR)
Routers extend the network’s reach and reliability, and:
- Forward messages between devices (mesh networking)
- Can allow other devices to join the network
- Must remain powered continuously to maintain network integrity
- Include devices like smart plugs, smart bulbs (when powered) and wired sensors
Zigbee End Device (ZED)
End devices are typically battery powered sensors and controllers, which:
- Cannot route messages for other devices
- Sleep most of the time to conserve battery
- Wake periodically to check for messages or send data
- Include devices like door sensors, motion detectors, wireless switches and remote controls
End devices communicate directly with their parent router or coordinator. If the parent fails, they automatically search for a new parent to re-join the network. This is all part of Zigbee’s self-healing design.
How Zigbee’s Mesh Network Works
Unlike Wi-Fi, where every device connects directly to your router, Zigbee creates a mesh network. Think of it like a relay race. Messages pass from device to device like runners handing off a baton, extending your reach far beyond what any single device could achieve.
Why This Matters
If your hub in the living room can’t directly reach a sensor in the garage, no problem. The message hops through the smart plug in the hallway and the bulb in the kitchen to get there.
The Self-healing Part
If one device fails or loses power, the network automatically reroutes around it. Your sensor in the garage will just find a different path through your mesh.
Keeping Your Zigbee Network Secure
Zigbee takes security very seriously. All communications are encrypted with industry standard 128-bit AES encryption. Here’s what you need to know.
Built-in Protection
Modern Zigbee (version 3.0 and newer) requires install codes when adding new devices. Your hub acts as the network’s security manager, controlling which devices can join and encrypting all communications.
What Zigbee PRO 2023 Added
The latest 2023 update introduced smarter security. Instead of using the same encryption keys forever, devices now use dynamic keys that change. Your hub can also “interview” new devices before letting them join, checking if they’re legitimate and up-to-date. Plus, if your hub dies, you can now replace it without re-pairing every single device (an enormous time saver for most).
Simple Security Checklist for Home Users
- Buy Zigbee 3.0 certified devices (they have the latest security features)
- Change any default passwords on your hub immediately
- Enable automatic firmware updates
- Remove old devices from your network when you’re done with them
- Keep accessible devices (like outdoor sensors) physically secure
Best Practices for Zigbee Network Deployment
New to Zigbee? Your 5 Minute Setup Checklist
Starting your first Zigbee network? Follow this quick checklist to get up and running ASAP.
- Step 1: Position Your Hub/Coordinator – Place it centrally if possible, or near your Internet router if needed for connectivity. This becomes your network’s foundation.
- Step 2: Add 2-3 Always-Powered Routers First – Smart plugs work perfectly. Place them strategically throughout your home to extend coverage. These create your mesh network backbone.
- Step 3: Select Your Zigbee Channel – Check your hub settings and pick a channel that avoids Wi-Fi interference. Channels 15, 20 or 25 usually work well. Let your hub auto-select if you’re unsure.
- Step 4: Pair Your Router Devices – Add those smart plugs and powered bulbs to the network first. They’ll route messages for battery devices you add later.
- Step 5: Add Battery Powered End Devices – Now pair your sensors, wireless switches and battery powered devices. They’ll automatically find nearby routers to connect through.
- Step 6: Test Your Coverage – Place a sensor in your furthest room. Does it respond? If not, add another router between that room and your hub.
- Step 7: Done! – Your network is live. Add more devices anytime. They’ll automatically join the mesh.
Troubleshooting Common Zigbee Issues
Running into issues? Don’t worry, even the best Zigbee networks have hiccups. Here are the most common problems and their solutions.
Devices Won’t Join the Network
Possible causes: Range issues, coordinator not in pairing mode, install code problems, network full
Solutions:
- Move device closer during pairing
- Verify coordinator is in pairing mode
- Double check install code entry
- Restart coordinator and try again
Intermittent Connectivity
Possible causes: Interference, router failure, poor mesh connectivity, range limits
Solutions:
- Check for new sources of 2.4 GHz interference (new Wi-Fi routers, baby monitors)
- Verify router devices are powered and functioning
- Add more router devices to strengthen mesh
- Use hub diagnostics to identify weak links
Devices Dropping Off Network
Possible causes: Power issues, interference, key rotation problems, device failure
Solutions:
- Replace batteries in end devices
- Check power supplies for router devices
- Verify successful key rotation
- Re-pair problematic devices
- Consider replacing failing hardware
Matter and Zigbee: Different Protocols, Working Together
You’ve probably heard about Matter, the new smart home standard promising universal compatibility. So what does that mean for your Zigbee devices?
The short answer: Your Zigbee devices aren’t obsolete. They’ll keep working.
Matter is a separate protocol that runs over Thread, Wi-Fi and Ethernet, not over Zigbee. They’re different technologies, but many smart hubs act as bridges between them. Your hub translates between your Zigbee devices (like Philips Hue bulbs) and Matter enabled apps, making everything work together in harmony.
What This Means for You
- Your existing devices keep working: No need to replace anything
- Your hub does the heavy lifting: It handles all the translation automatically
- Hundreds of millions of Zigbee devices remain supported and useful
- New devices might support both: Some come with dual capabilities built-in (not upgrades to old devices)
Zigbee isn’t going anywhere. The Connectivity Standards Alliance (which created both protocols) actively supports both. With its proven reliability, excellent battery life and massive installed base, Zigbee is an excellent choice for battery powered sensors and mesh networking.
The Buzz About Zigbee
Zigbee won’t grab headlines, but it will power your smart home reliably for years. With hundreds of millions of devices deployed worldwide, years-long battery life and self-healing mesh networks, it’s proven itself as the backbone of home automation.
And thanks to modern hubs that bridge Zigbee into Matter, your existing devices continue to stay relevant as the smart home evolves.
Reliable. Efficient. Quietly brilliant. That’s the real buzz about Zigbee.